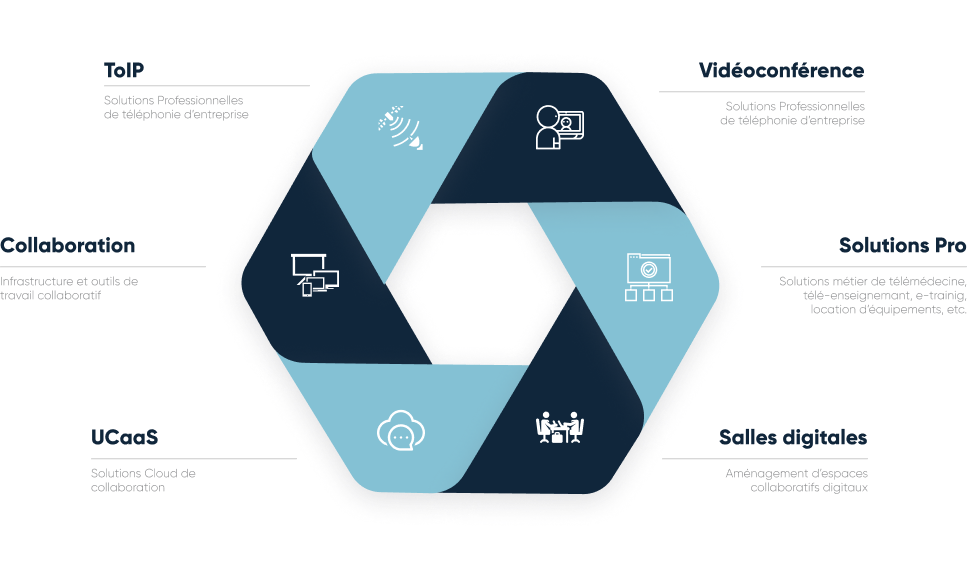
Our expertise
Our offer can align the performance of your information system with your business requirements, allowing you to provide your products and services to your internal and external customers with an increased quality of service, in a reduced time (Time To Market). Our offer goes hand in hand with our mission to improve IT performance and includes innovative solutions and services for infrastructures (networks, datacenter, cloud), users, security and the monitoring of the company’s assets.
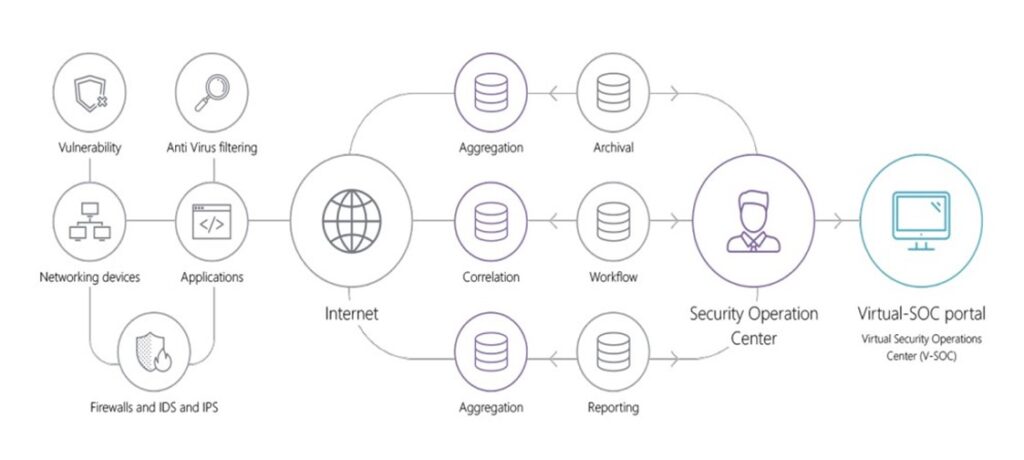
Nous proposons une approche cohérente de la gestion des menaces avec des solutions novatrices pour sécuriser les infrastructures et les données des entreprises.